No business leader likes to think of their own employees as a threat to information security. But the truth is, most threats stem from inside the organization, either at the hands of malicious intent or human error.
Regardless of how dependable and cutting-edge your technological controls are, they’re only ever as effective as your team is at using them. Employees are still, and likely always will be, the first and last line of defense. Technology, by contrast, makes it easier for them to do their bit to protect your digital assets, but it doesn’t replace human intuition and employee training.
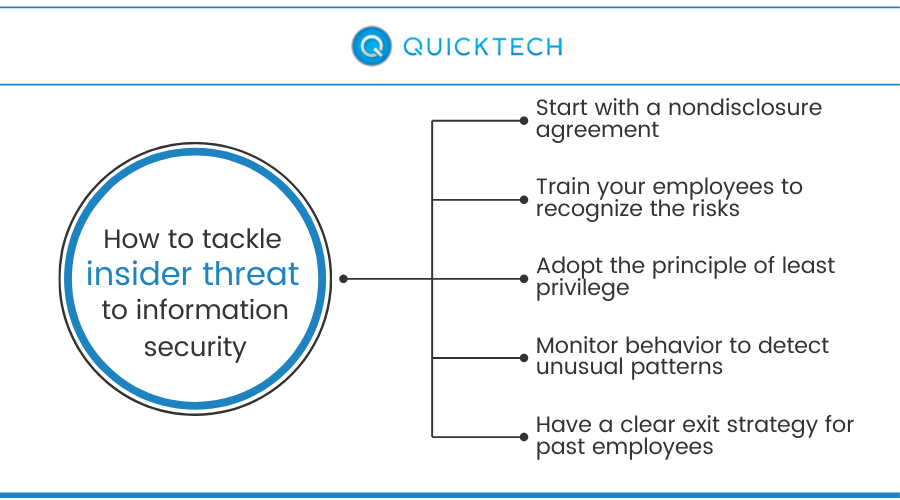
Here are the key steps you need to take to mitigate insider threat:
Start with a nondisclosure agreement
While policies and contracts aren’t likely to reduce insider threats by themselves, they do give you vital legal recourse should an event occur. For example, if someone deliberately divulges sensitive information they’ve committed to keeping under wraps by signing a nondisclosure agreement, you’ll have the legal right to take action. When it comes to regulated information, such as healthcare or payment data, having the right policy framework in place is also a legal requirement.
Train your employees to recognize the risks
Most insider threats aren’t malicious, although disgruntled employees are less likely to do a good job of upholding your security policies. No matter the case, training employees to better understand the risks is critical for mitigating human error, as well as intentional compromise of sensitive data. That’s why businesses should make security awareness training less about the company and more about the security of the people it works with — your customers and employees. Employees who have a deep understanding of the risks and are fully aware of their responsibilities won’t just be more vigilant, but they’ll also be able to work in confidence — which, in turn, means enhanced productivity and morale.
Adopt the principle of least privilege
There’s no need to give anyone on your team access to apps and data if they don’t absolutely need it for work. This isn’t just a matter of information security either — people work better if they’re not bombarded with information and apps. The principle of least privilege holds that no one should ever have clearance for accessing assets they don’t require for their jobs. It also helps restrict sharing data over unsecured channels while giving administrators greater control and visibility over company apps and data.
Monitor behavior to detect unusual patterns
Firewall and antivirus software are no longer enough to protect the typical business network, particularly in the age of workforce mobility and mobile and cloud computing. Administrators need a centralized dashboard for monitoring access rights and behaviors over increasingly large and complex operational environments. By adding artificial intelligence (AI) and real-time monitoring into the mix, you can more effectively detect unusual patterns and take proactive action before the risk reaches an unacceptable level.
Have a clear exit strategy for past employees
One of the biggest threats to information security comes from disgruntled employees leaving the company on bad terms. This might involve them taking away a company-issued laptop or smartphone or failing to remove their access tokens from their own devices that they used for work as well. You need a clear exit strategy that allows employees to voluntarily disenroll from your BYOD and other programs and, if necessary, this may need to be enforced by an administrator if the employee fails to comply with your policy.
Quicktech helps businesses protect themselves from insider threats and other digital dangers with round-the-clock monitoring and more.

Like this article?
Sign up below and once a month we'll send you a roundup of our most popular posts